Description
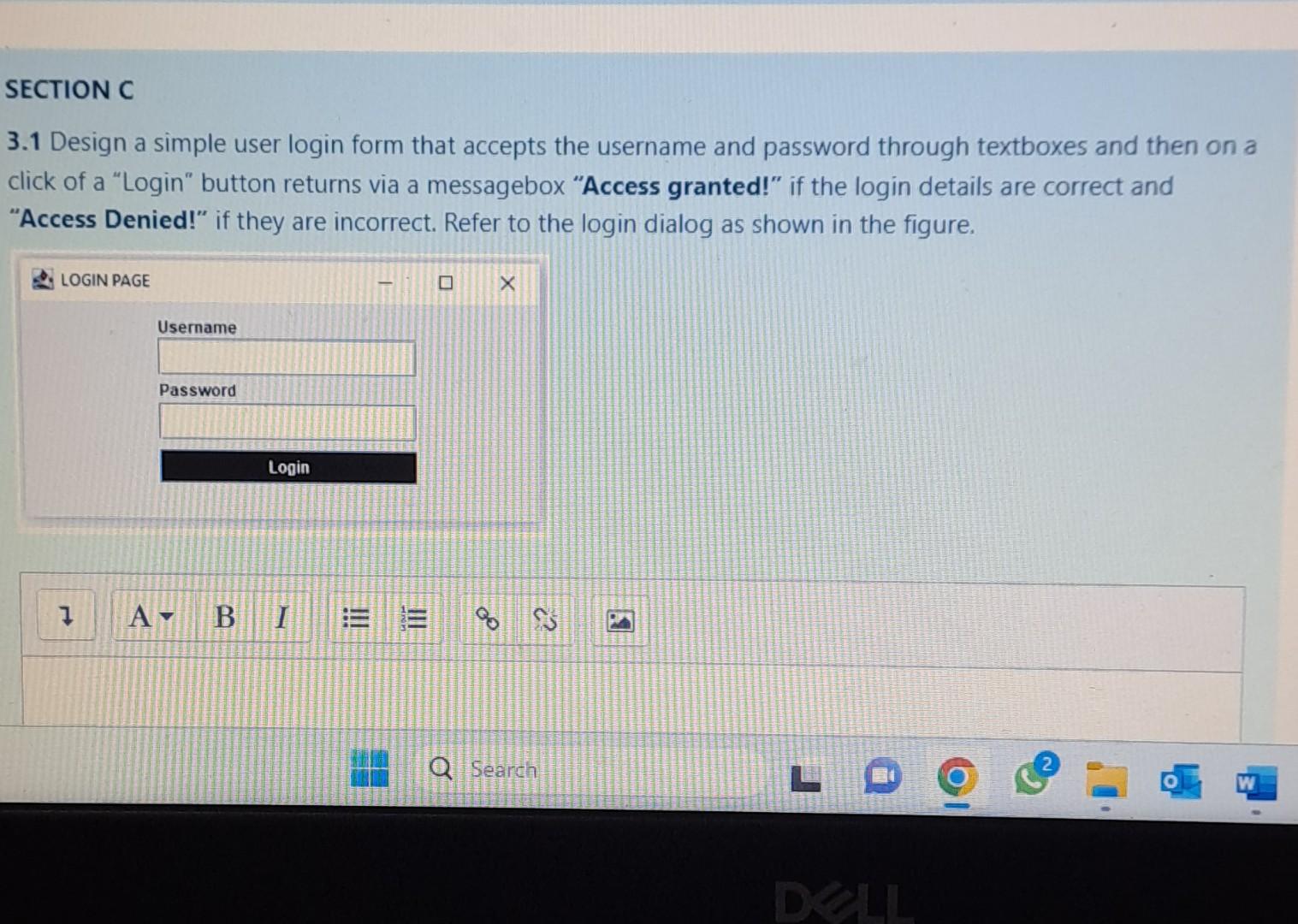
Design a simple user login form that accepts the username and password through textboxes. On clicking a “Login” button, display a messagebox with the message “Access granted!” if the login details are correct. Display “Access Denied!” if the login details are incorrect. Refer to the login dialog shown in the figure.




![Sure, here is the Python program A1Q2.py that displays formatted messages based on the given instructions: ```python def display_message(): # Step 1: Ask user to input a string message user_input = input("Enter a string message, including your name and a short message (less than 40 characters): ") # Step 2: Ask user to input a field width greater than 40 width = int(input("Enter a positive integer greater than 40 as a field width: ")) # Step 3: Ask user to input an alignment method alignment = input("Enter an alignment method [left, right, center]: ") # Step 4: Format and display the message print("+" + "-" * width + "+") formatted_message = f"|{user_input:{alignment}{width-2}}|" print(formatted_message) print("+" + "-" * width + "+") # Call the display_message function display_message() ``` This program prompts the user to input a string message, a field width greater than 40, and an alignment method. It then formats and displays the message inside a box according to the given width and alignment. The box is created using '+' and '-' characters. Note that the program assumes valid inputs from the users, such as a string message that is less than 40 characters including the name, a positive integer greater than 40 as the field width, and a valid alignment method ('left', 'right', or 'center'). You can run this program by saving it as A1Q2.py and executing it using a Python interpreter.](https://gotit-pro.com/wp-content/uploads/2023/10/e2fd92a3-2720-4c80-abe3-f2461c53bbdf.jpg)





Stephanie Specht –
It was amazing work and in a very short time.
Edward Parker –
Great quality solution, Done way before time
Andrew Porteck –
great work as usual thanks
Julie Redd –
Tutor wrote it quickly and effectively. Great solution.
Chris Aikins –
Great Work In Timely Fashion. Something what I wanted.
Haze Clifford –
great and amazing work, highly recommend. God bless you in all your days