Subtotal: $30.00
 Create a program that generates 1000 random integers between 1 and 100 (both included) and save them into a list.
Original price was: $10.00.$5.50Current price is: $5.50.
Create a program that generates 1000 random integers between 1 and 100 (both included) and save them into a list.
Original price was: $10.00.$5.50Current price is: $5.50.
 Write a program that first reads in the name of two input files; input1pass.txt and input1shadow.txt. These files will contain encrypted and non-encrypted passwords to simulate a Brute Force approach.
Original price was: $14.00.$10.00Current price is: $10.00.
Write a program that first reads in the name of two input files; input1pass.txt and input1shadow.txt. These files will contain encrypted and non-encrypted passwords to simulate a Brute Force approach.
Original price was: $14.00.$10.00Current price is: $10.00.
Write a program that first reads in the name of an input file, reads the information stored in that file and determines if the user login has occurred at off hour times.
Original price was: $7.00.$5.00Current price is: $5.00.
-29%Download button will appear immediately after successful payment.
Book your next exam with us and get A+ in entire semester, guaranteed!
Securing a network from attacks means a network administrator is watching traffic and user activity. Change detection (CD) is a method used to track changes in your network. CD can detect files accessed during off hours to more complex algorithmic detections added to software applications that manage this process.
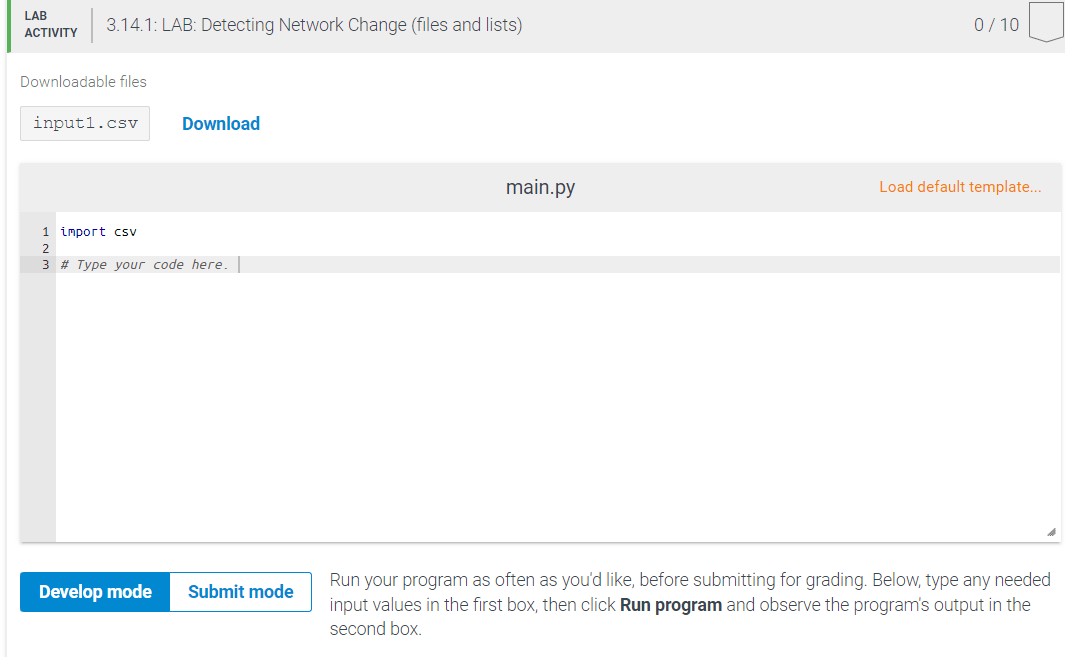
This program is going to manage user login times and attempt to detect any change in a users typical login attempts. It will use an input file to store data and read the file using the csv.reader( ) method. The file will contain a list of login_names, followed by login_time separated by commas.
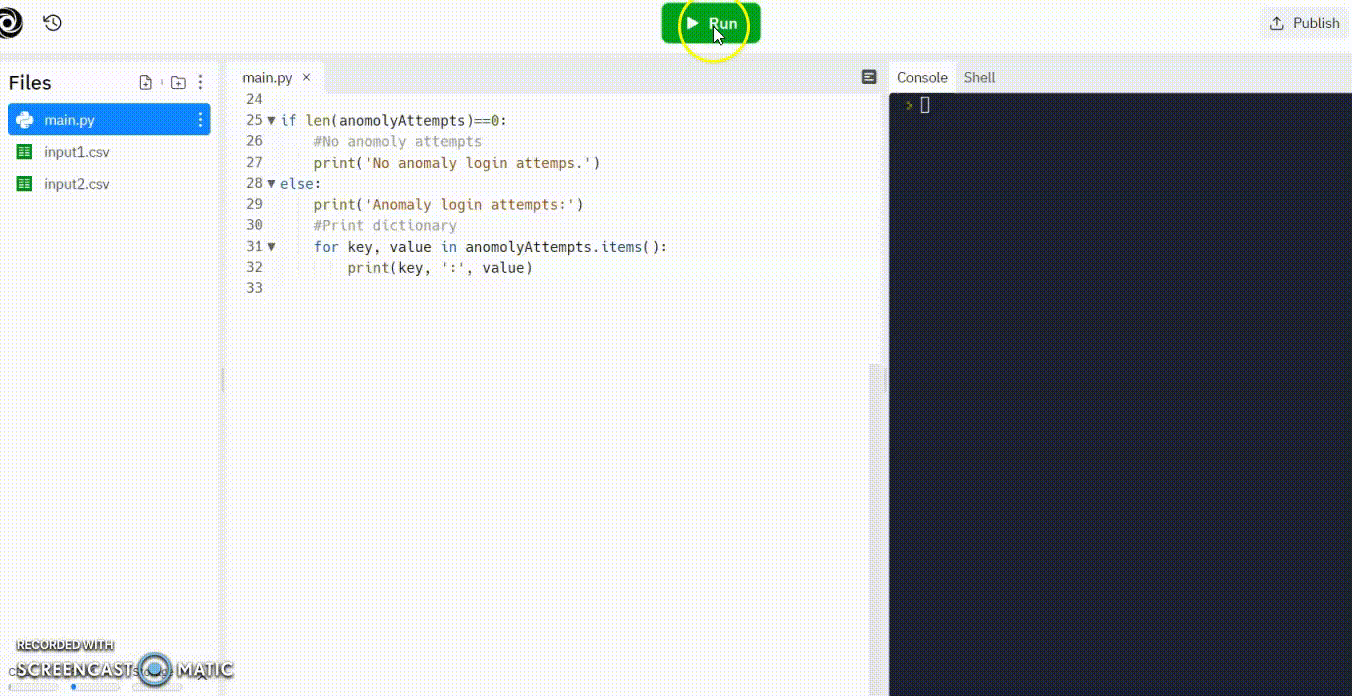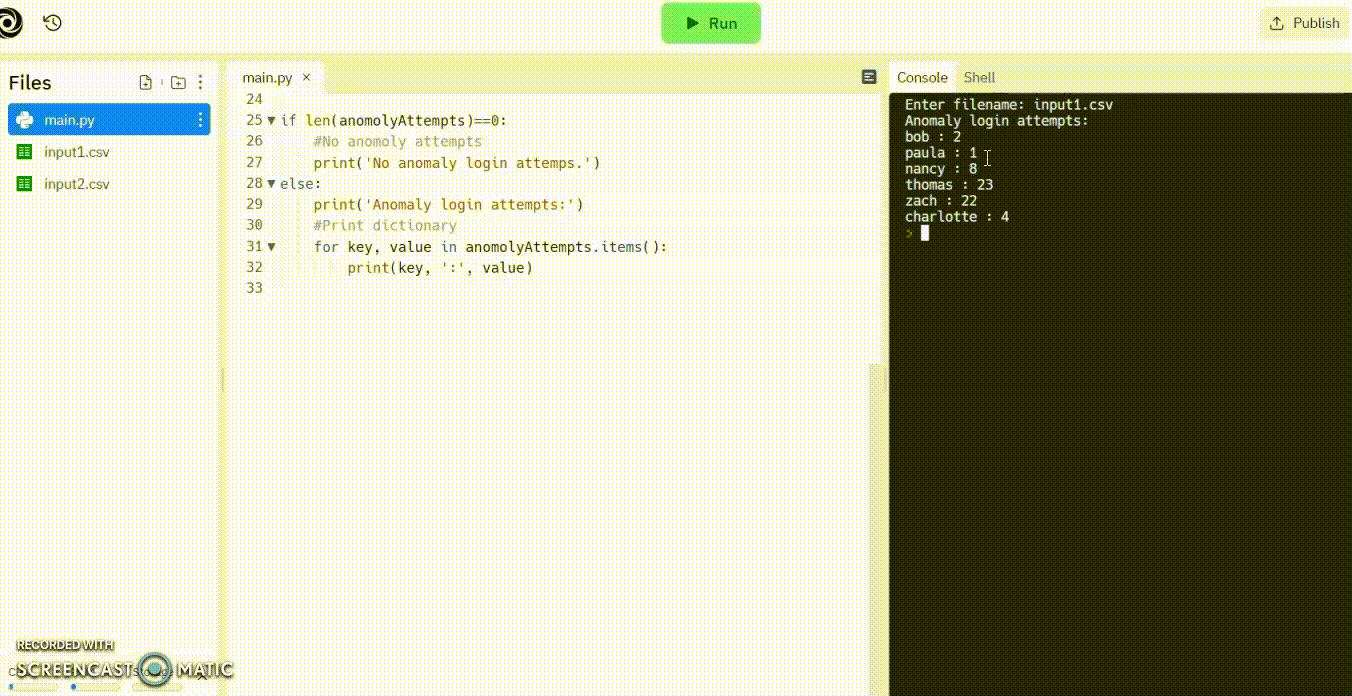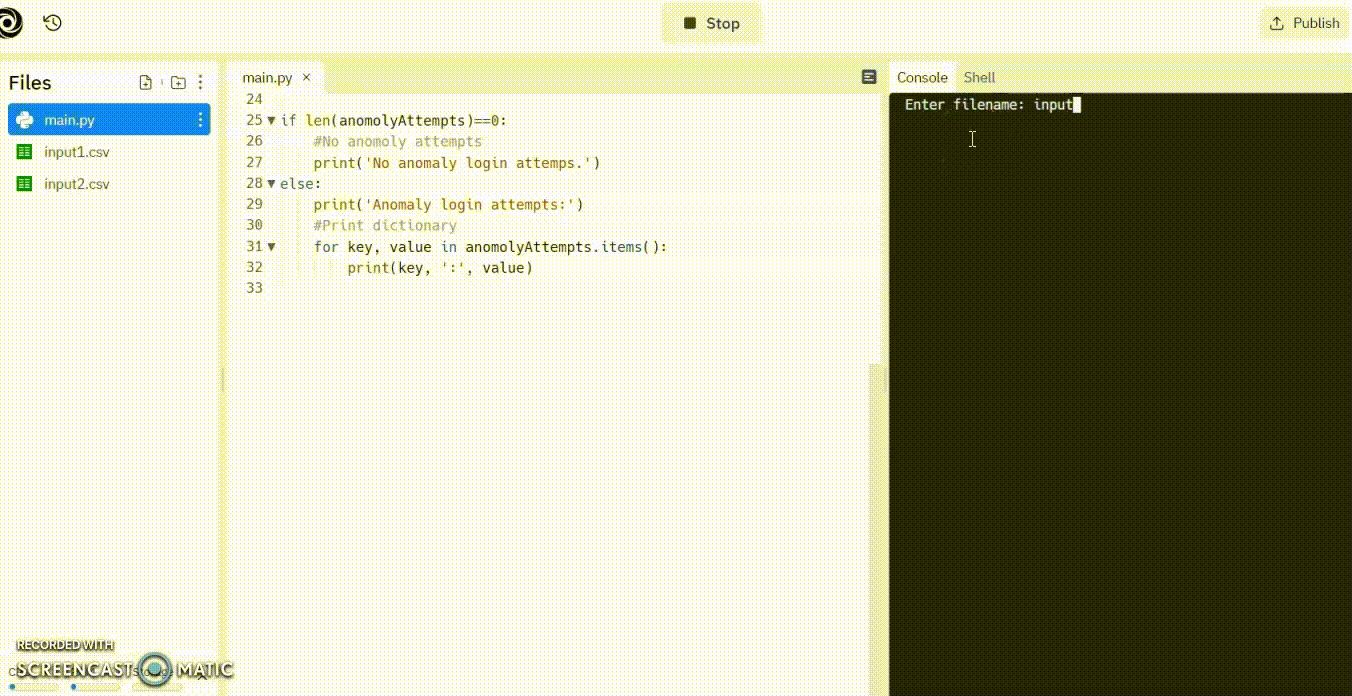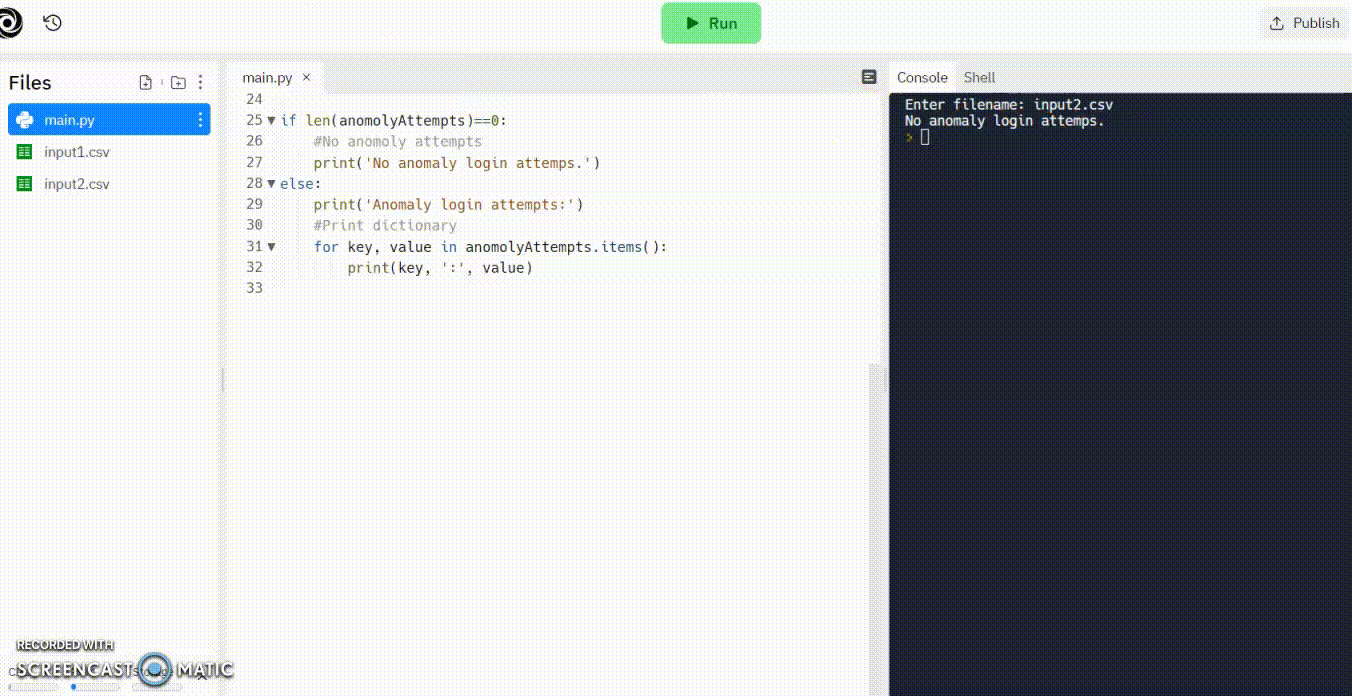
Write a program that first reads in the name of an input file, reads the information stored in that file and determines if the user login has occurred at off hour times. The company employees work from 9 am to 5 pm so any other time would be an off hour login attempt. If the login attempt is made after hours, store the user name and login time in a dictionary with the user name as the key. Display all anomaly attempts at the end of the program. If there are no questionable login attempts display No anomaly login attempts
Ex: If the input is:
input1.csv
and the contents of input1.csv are: (store time as integers and use military time to simulate am and pm attempts)
bob,2,paula,1,nancy,8,thomas,23,zach,22,charlotte,4
the output is:
Anomaly login attempts:
nancy:8
thomas:23
zach:22
charlotte:4
Ex: If the input is:
input2.csv
and the contents of input2.csv are: (store time as integers and use military time to simulate am and pm attempts)
the output is:
No anomaly login attempts
Note: There is a newline at the end of the output, and input1.csv is available to download.
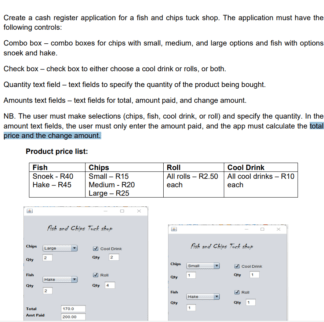 Create a cash register application for a fish and chips tuck shop. The application must have the...
Create a cash register application for a fish and chips tuck shop. The application must have the... 



Kathy Henley –
I got 96% on this assignment. Anything above 95% is great in my book!
Glenn Mccall –
Great service! I had an assignment theory to be done and wasn’t specific enough from my side on what I exactly needed it for. Even after messaging the expert one day before, they had it done the next day by the time I requested last minute.